| | | | | | | | | | | Axios Codebook | | By Megan Morrone · Oct 15, 2024 | | Hello, Tuesday! Welcome back to Codebook. - 🏝️ Sam will be back in your inboxes on Friday. For now, you still have me, Megan.
📬 Have thoughts, feedback or scoops to share? codebook@axios.com. Today's newsletter is 889 words, a 3.5-minute read. | | | | | | 1 big thing: What you need to know about Salt Typhoon | | By Megan Morrone | | |  | | | Illustration: Eniola Odetunde/Axios | | | | The Salt Typhoon cyberattack that reportedly targeted U.S. wiretap systems could be one of the most damaging China-backed cyber espionage campaigns ever, per the Wall Street Journal. Why it matters: The hack may have given the Chinese government unprecedented access to U.S. foreign-intelligence surveillance systems and electronic communications that major internet service providers like Verizon and AT&T collect based on U.S. court orders. Threat level: The hackers were able to attain highly sensitive intelligence and law enforcement data, per reports. - Jamil Jaffer, a former White House national security official and executive director of the National Security Institute at the George Mason University's Scalia Law School, told the Wall Street Journal that this could be "a counterintelligence failure of the highest order."
Catch up quick: Salt Typhoon is only one of several advanced persistent threats (APTs) believed to be backed by Beijing. - There are several "typhoon" threats, the moniker used by Microsoft to track different Chinese-backed campaigns based on their tactics and procedures.
- Salt Typhoon has been active since 2020, according to Microsoft research cited by the Journal.
- Volt Typhoon has persistently infiltrated U.S. infrastructure, with reports showing that attackers maintained access to critical U.S. systems for "at least five years."
- Flax Typhoon targets home routers, firewalls, storage devices, and Internet of Things devices like cameras and video recorders and has been active since 2021, according to the Department of Justice.
Between the lines: Salt Typhoon reportedly gained access to Verizon, AT&T and Lumen Technologies by exploiting systems used for lawful wiretapping, which are designed to comply with government surveillance requests. - The Electronic Frontier Foundation says the backdoors used by Salt Typhoon were likely created to help companies comply with the Communications Assistance for Law Enforcement Act (CALEA), which requires telecommunications companies to cooperate with legal orders by law enforcement and national security agencies.
Zoom out: Critics of legally mandated backdoors intended for lawful surveillance have always argued that bad actors will eventually find ways to compromise such designs. What they're saying: Last week, Sen. Ron Wyden (D-Ore.), a frequent critic of government surveillance techniques, sent a letter to FCC Chairwoman Jessica Rosenworcel and Attorney General Merrick Garland urging the DOJ to "recognize the failure of its current approach to combating cyberattacks" and investigate cybersecurity practices at companies that were attacked. - Bipartisan leaders in the House Energy and Commerce Committee wrote letters to the CEOs of AT&T, Verizon and Lumen Technologies asking them to explain how the incident occurred and what steps the companies were taking to secure customer data.
- Chairman John Moolenaar (R-Mich.) and Rep. Raja Krishnamoorthi (D-Ill.) of the House Select Committee on the Strategic Competition Between the United States and the Chinese Communist Party also sent a letter to the CEOs, requesting a closed-door briefing to learn more about when the companies discovered the attack.
|     | | | | | | 2. Wayback Machine back up after DDOS attacks | | By Scott Rosenberg | | | 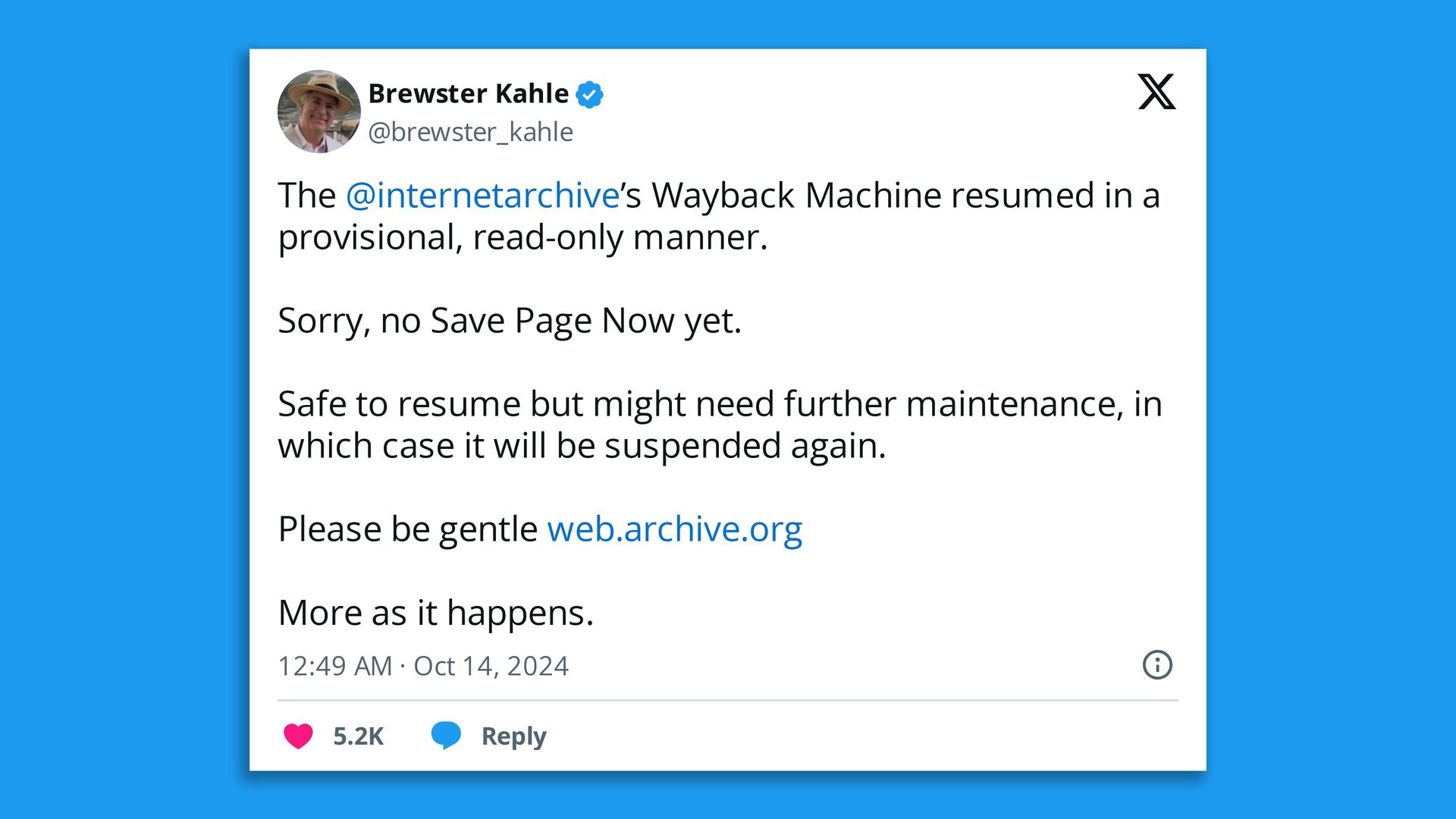 | | | Screenshot: X/@brewster_kahle | | | | The Internet Archive was back up yesterday, with some limits, after spending nearly a week offline following a data breach and distributed denial-of-service attack. Why it matters: The archive and its Wayback Machine are a unique, irreplaceable resource recording decades of web history. - Founder Brewster Kahle posted on X: "The @internetarchive's Wayback Machine resumed in a provisional, read-only manner.... Please be gentle."
Catch up quick: The attack on the archive became public Oct. 9, when visitors to the site were met with a taunting popup that read, "Have you ever felt like the Internet Archive runs on sticks and is constantly on the verge of suffering a catastrophic security breach? It just happened. See 31 million of you on HIBP!" - HIBP is the Have I Been Pwned site, which lets users look up whether their personal data has been compromised by data breaches.
- That site's operator told BleepingComputer it had received a 6.4 GB database file containing "authentication information for registered members, including their email addresses, screen names, password change timestamps, Bcrypt-hashed passwords, and other internal data."
The intrigue: With the data breach made public, the Internet Archive also found itself faced with one or more DDOS attacks that kept users from accessing the site. - A motive for the attacks on the archive, a nonprofit organization beloved by researchers, has not been identified.
|     | | | | | | 3. Catch up quick | | | | @ D.C. ✨ The United Nations Office on Drugs and Crime released a report outlining the way AI is boosting cyber-enabled fraud and cybercrime, especially digital scamming known as pig butchering. (Wired) @ Industry 💸 A Florida data broker leaked millions of Social Security numbers. Now it's filing for bankruptcy. (PCMag) @ Hackers and hacks 🔑 Chinese researchers say they've cracked RSA encryption with the D-Wave quantum computer. RSA encryption helps protect web browsers, virtual private networks, email services and popular electronics brands' chips. (CSO Online) 👾 A popular Pokemon game developer confirmed that its systems were hacked and that personal details of employees were leaked, but it did not confirm that the leak included unreleased Pokemon content, as had been previously reported. (The Record) 📟 Japanese electronics maker Casio has been hacked. The attackers accessed sensitive technical information, employee information and some customer information. (TechCrunch) |     | | | | | | A message from Axios HQ | | 3 free Smart Brevity® workbooks | | |  | | | | As organizations grow, communication can break down. This impacts engagement, productivity, and your bottom line. Smart Brevity breaks through and keeps teammates engaged with - 40% shorter emails, on average
- 100% of the insights they need
We boiled down the basics into three workbooks. Get the bundle | | | | | | 4. 1 fun thing | | | 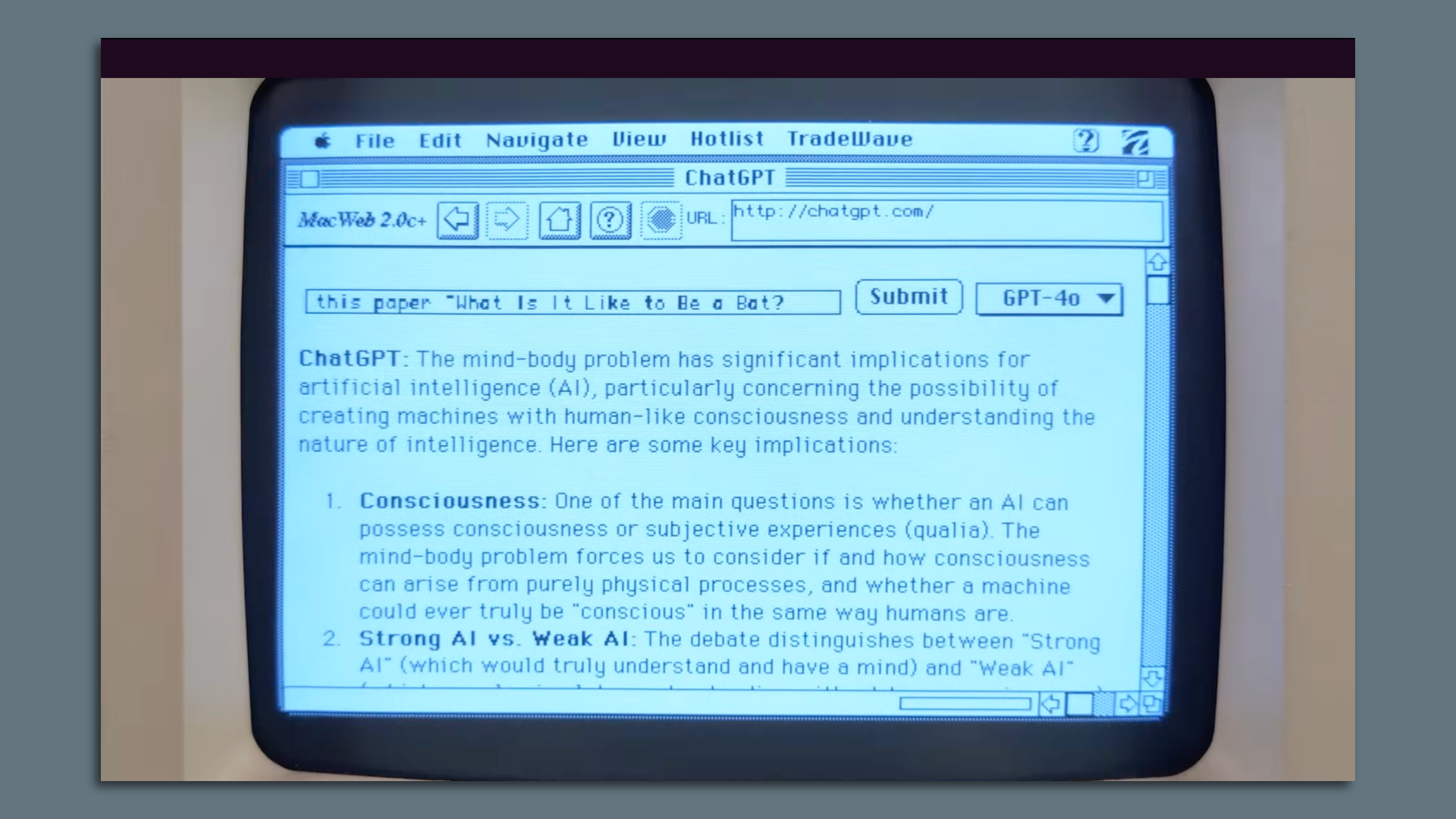 | | | ChatGPT running on an original Apple Macintosh Plus. Screenshot: YouTube | | | | YouTuber Hunter Irving found an original Apple Macintosh Plus at a thrift store, and after turning it on and popping a capacitor that filled his home with smoke, he managed to connect the Mac Plus to the internet using a Raspberry Pi. |     | | | | | | A message from Axios HQ | | Run your org on Smart Brevity® | | | /2024/09/27/1727466727224.gif) | | | | Axios HQ's Smart Brevity trainers and editors have worked with 20,000+ professionals to elevate workplace comms. They partner with orgs – big and small — to: - Understand and apply Smart Brevity
- Make key internal comms actionable
- Track progress along the way
▶️ See how Smart Brevity works | | | | Thanks to Scott Rosenberg for editing and Khalid Adad for copy editing this newsletter. If you like Axios Codebook, spread the word. |  | Your essential communications — to staff, clients and other stakeholders — can have the same style. Axios HQ, a powerful platform, will help you do it. | | | |

0 comentários:
Postar um comentário